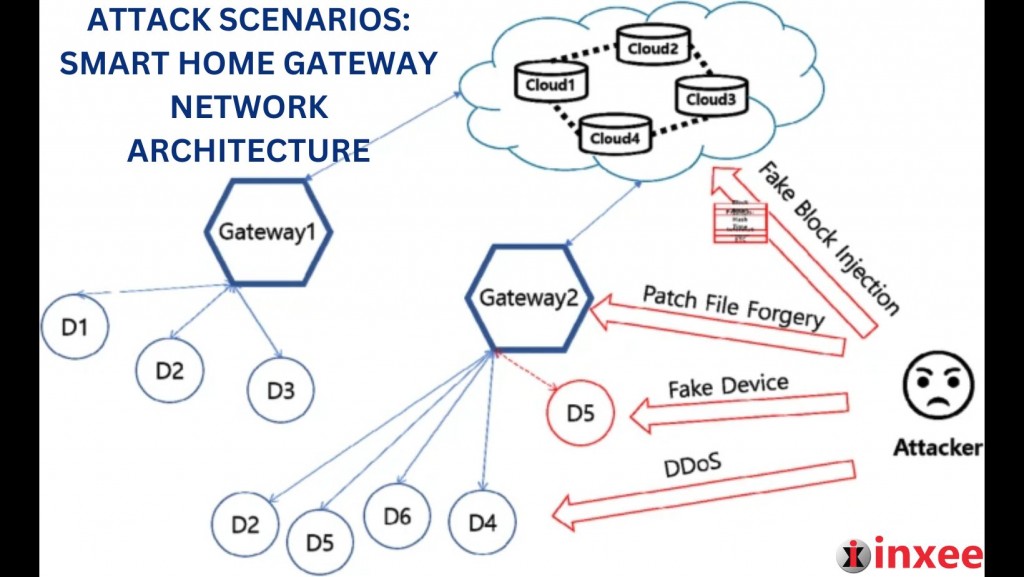
Attack Scenarios Smart Home Gateway Network Architecture
Security analysis: Attack techniques on existing smart home gateways are continually changing as the environment changes to the network and the IoT. Especially, IoT devices have limited computing power and battery capacity. In this network environment, an attacker can set various attack scenarios according to the target device.
Patch file forgery attack: A forgery attack against a patch file is a method of attacking a specific device through a connected router or the patch file itself. In the proposed architecture, if a patch is applied to a device through a tampered patch file, it can result in device malfunction, permission change, eavesdropping, and data deletion. The proposed architecture ensures the integrity of centrally distributed patches for batch updates of devices and strengthens the security of the management server itself.
ZeroDay Attack: Zero-day attack is a technique that attacks when a patch for a software vulnerability is not available. Because of the lack of countermeasures possible against such vulnerabilities, such attacks cannot be prevented, and any device can be compromised. The proposed architecture supplements with periodic security updates, whitelists and blacklists, and blocks attacks through real-time monitoring of changes.
Blockchain 51% Attack: It is a hacking attack that attempts to profit by manipulating transaction information after securing more than 50% of the hash nodes of the entire blockchain nodes. In other words, a 51% attack means that a malicious attacker has powerful hash computing power more than 50% of the whole network. The attacker can create new blocks and add them to the blockchain network faster than other honest nodes so that other nodes can store forged data. The attack forces other blocks to adopt a blockchain that contains forged data. However, for the 51% attack to succeed in the proposed blockchain-based architecture, the hash power of all nodes participating in the blockchain network must be greater than the sum of the hash computation power. In addition, the number of nodes participating in the architecture increases, which can effectively defend against attacks. Therefore, the blockchain 51% attack on the proposed blockchain-based architecture is impossible.
DDoS: Distributed Denial of Service (DDoS) attack results in the disruption of services provided by a server by flooding it with traffic from compromised devices. If an attack occurs on an existing centralized smart home gateway network, authentication and integrity services are stopped. The proposed architecture prevents DDoS traffic during data processing by not providing loops such as If/While/for in basic IoT request scripts. Applying the resource consumption limit of blockchain, the attacker cannot proceed indefinitely. In addition, DDoS attacks on the entire blockchain network are impossible on all nodes at once. This depends on the environment in which the nodes are distributed.









Leave a Reply