Iot Security Attacks
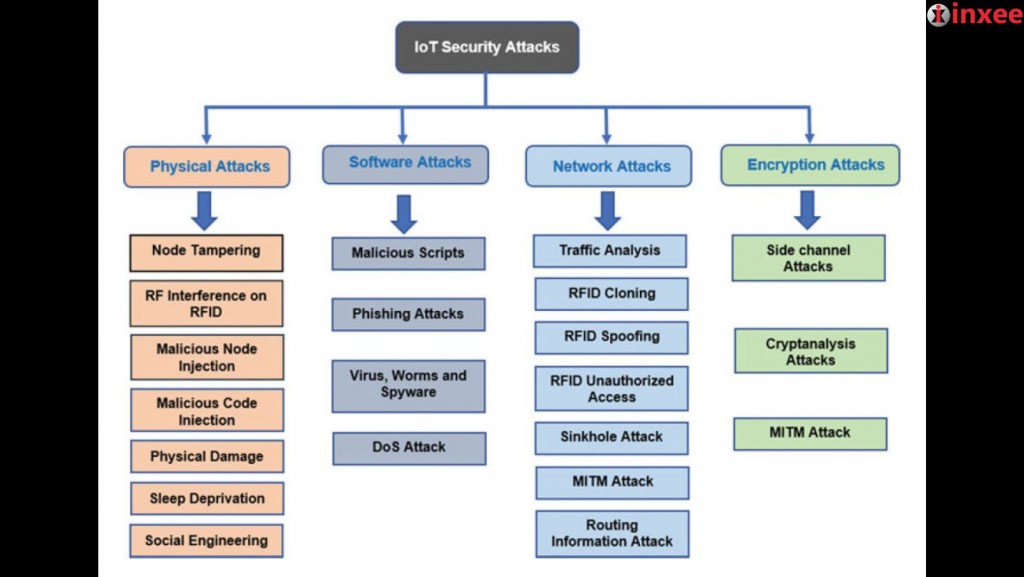
IoT (Internet of Things) security is a major concern as it deals with a large number of devices and networks that are connected to the internet. Attackers can use various methods to compromise the security of IoT devices and networks. Let’s take a look at the different types of IoT security attacks:
Physical Attacks: Physical attacks involve gaining unauthorized access to an IoT device or network by physically accessing it. This can include tampering with sensors or stealing the device itself. Physical attacks can also include denial of service (DoS) attacks, which involve overloading the device with traffic to make it unusable.
Software Attacks: Software attacks involve exploiting vulnerabilities in the software used by IoT devices and networks. Hackers can use malware or viruses to gain access to the device or network, steal data or damage the device. These attacks can also include cross-site scripting (XSS) attacks, which involve injecting malicious code into web pages to steal data.
Network Attacks: Network attacks involve exploiting vulnerabilities in the network used by IoT devices. Hackers can use techniques such as sniffing, spoofing, and man-in-the-middle (MITM) attacks to intercept data, modify it, or redirect it to another location. Network attacks can also include distributed denial of service (DDoS) attacks, which involve using a large number of devices to flood a network with traffic, making it unavailable.
Encryption Attacks: Encryption attacks involve exploiting weaknesses in encryption protocols used by IoT devices and networks. Attackers can use various techniques such as brute force attacks to decrypt sensitive information. They can also intercept encrypted data and use it to gain access to the network or device.
To protect against these attacks, IoT devices and networks need to implement strong security measures such as encryption, access controls, and intrusion detection systems. It is also important to keep software and firmware up to date to protect against known vulnerabilities. Additionally, users should be educated on how to use IoT devices securely and understand the risks associated with them.









Leave a Reply